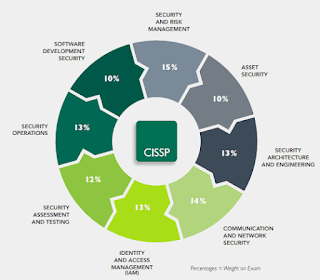
8 Domains of information Security for Your ISMS
- Security & Risk Management
- Asset Security
- Security Engineering
- Communication & Network Security
- Identity & Access Management
- Security Assessment & Testing
- Security Operations
- Software Development Security
1 Security & Risk Management :
Establishes the security policies, procedures, guidelines, structures and standards to protect information assets and to review the effectiveness of the security controls.
2 Asset Security :
Establishes the procedures, structures & standards, and controls used to secure and monitor assets to enforce confidentiality, integrity and availability.
3 Security Engineering:
Establishes the concepts, structures & standards to design and implement secure systems, networks and applications to enforce confidentiality, integrity and availability.
4 Communication & Network Security:
Encompasses the structures, transmission methods, transport formats, and security measures used to provide confidentiality, integrity and availability for communications over private and public networks and media to ensure confidentiality, integrity and availability.
5 Identity & Access Management :
Access controls encompass securing access to business operations, systems and information assets.
6 Security Assessment & Testing
Describes various methods based used to determine vulnerabilities & associated risk evaluation.
7 Security Operations
Identifies critical Information and measures that will eliminate or reduce exploitation of the information. Includes controls, access privileges, monitoring and auditing processes.
8 Software Development Security:
Enforce security controls in the software development life-cycle to ensure software security.?
Niranjan Meegammana



Comments
Post a Comment